Review: Track and Protect
Score:
85%
Rafe takes a look at Track and Protect, a solution which aims to provide a remote management and tracking solution for consumers.
Version Reviewed: 1
Buy Link | Download / Information Link
Introduction
Our mobile phones contain valuable information. Your SIM card, with its associated number, is an all-important point of contact. Then there's the content, it's not just about contacts any more, there are text messages, emails, photos, music, applications and more too. Chances are your phone has stored log-ins for your social networking accounts, giving easy access to Twitter, Facebook and more. It's not just about the lost content, but also the access to your personal identity and online presence. It's no surprise then that an ever increasing number of people say that their mobile is one of their most important possessions. Moreover, the mobile phone is a vulnerable object; it goes with you everywhere, gets waved about in public and is small enough that it's easily lost or stolen. Many of us have experienced that feeling of dread when you've been parted from your phone. If you have been fortunate so far, it may only be a matter of time.
In the enterprise world, IT managers, concerned about the security risk that mobile devices pose to corporate security, have long invested in remote management and security technologies. However, such solutions are usually expensive and tricky to set up and are, consequently, beyond the reach of most consumers. Moreover they are tailored to the enterprise environment, where data security, rather than retrieval, is the primary concern.
Track and Protect
This is where a new solution, Track and Protect from Klomptek, comes in. Track and Protect is a consumer-focussed, software and service combination that provides a security solution with remote management and location services. But what does this actually mean for the consumer? It provides a way for you to protect the contents of your phone if it is lost or stolen and to track its location. We'll explore this in more detail in the rest of the review. Track and Protect consists of two components, an application you install to your phone and an accompanying web site. The application handles security on the phone, while the web site provides a way to control the phone (the remote management portion) and track its location on a Google Map.
When you first install Track and Protect, you are walked through a simple set up procedure. You'll be asked to provide various pieces of information, including your phone number, email address and a security PIN. After this has been entered, the application contacts the Track and Protect server and sets up an account for you. And that's it! With the service activated, you are invited to visit the Track and Protect web site where you can log into your account and start using the remote management and location tracking features. It really is an impressively short and straightforward set up procedure, which should take you no more than a few minutes.
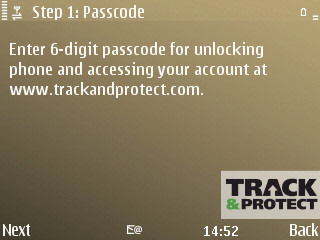
The basic security feature of Track and Protect is the lock screen at which you must enter your security PIN to continue using the phone. There are a number of optional settings, including controlling when you want the phone to be locked (i.e. times at which you'll have to enter your security PIN). These include 'lock at switch on', 'lock in offline' (you want the phone online so remote commands can get though), 'passcode check' (locks once, twice, or three times a day), and 'block uninstall' (locks when you access App. manager). Whether you choose to enable or disable these locks is entirely up to you, but I would recommend keeping the 'lock in offline' and 'block uninstall' as a minimum, as they are necessary to maintain full security in the time between losing the phone and activating a remote lock.
Basic security is fine, but once you've lost your phone, what you really want to do is lock it down immediately, to prevent any further use. This is where the remote management features of Track and Protect provide the solution. Once you have logged in to the Track and Protect website, using your phone and security PIN, you can send commands to the phone. These commands are sent as 'silent' text messages. The phone receives the text message, but it is intercepted by Track and Protect, and thus there's no sound, no notification of a tell-tale text message sitting in your inbox. Within a few seconds the Track and Protect application implements the appropriate command.
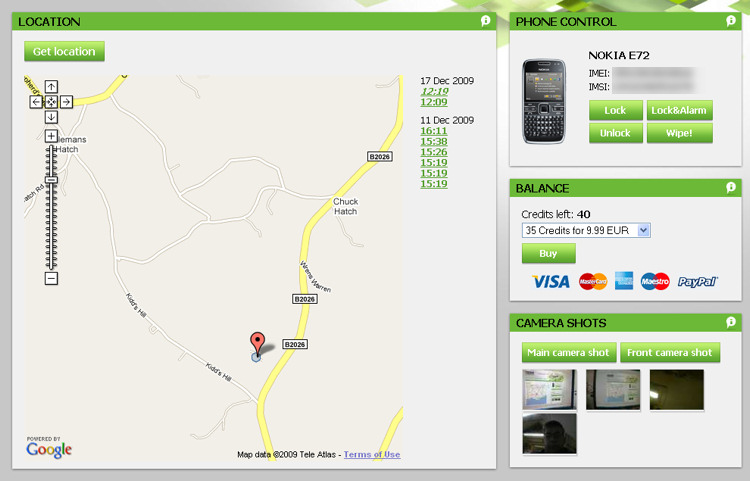
The main security commands include 'lock', 'lock and alarm', 'unlock', and 'wipe'. The 'lock' command causes the remote lock screen to be displayed, the 'lock and alarm' command does the same with addition of playing a loud alarm sound, and the 'wipe' command will delete all the data on your phone. The remote lock screen is slightly different from the everyday lock screen. It displays owner and reward information, but more importantly it allows for calls to be made, but only to three user specified numbers. This means that if someone finds the phone they can still call you to arrange to return the phone, but they can not use it for anything else. These numbers (home phone, work phone, friend's phone) can be set in the application settings along with the owner and return reward information. This well thought through implementation is typical of Track and Protect; it is clear that a lot of thought and experience has gone into creating a solution that works in the real world.

Remotely locked - but note the 'Call' button bottom right.
The location tracking features of Track and Protect are also enabled by the remote command system. Sending a 'get location' command to the phone returns the phone's current location to the Track and Protect server, which is then displayed on a Google Map. The phone will provide a location intelligently - if the phone has a GPS and if it is able to get a precise lock within a few minutes it will return a precise location, otherwise it will return a more general location based on the current cell ID. Obviously, getting location information is especially useful if you have misplaced the phone, but even if it is stolen it can still be useful. The more information you provide the the police, the more likely they will be willing and able to do something about it.
Adding to this 'more information is better' mantra is the remote command for camera capture. You can choose between the front camera and the rear camera, with the pictures returned over a data connection to the Track and Protect servers. These images may help you track down a lost phone or capture a thief unaware. Incidentally, a picture capture event is also triggered when you enter the security PIN incorrectly three times - precisely the moment someone is most likely to be looking at the front camera...
A critical test of such security applications is how easy it is to get around them. As noted earlier, Track and Protect can provide protection against being uninstalled and against offline mode. Assuming you enable all the lock scenarios, about the only issue I could come up with during testing was that you could remove Track and Protect by resetting the phone (*#7370# from the homescreen). However, this would have to be done before the phone was remotely locked, which leaves only a small window of vulnerability and you can 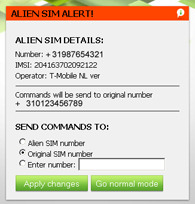 prevent this from happening by changing the default security code (in the phone's settings, from 12345).
prevent this from happening by changing the default security code (in the phone's settings, from 12345).
One of the common problems with remote security applications like Track and Protect is the 'Alien SIM' issue. This refers to the fact that such applications can stop working when an alternative SIM card is put into the phone. This is because remote commands, which are sent by SMS, can no longer be received because the phone number has been changed. Uniquely among the applications I have tried, Track and Protect does not have this problem because it recognises when a new SIM card has been inserted and notifies the server so that subsequent commands can, optionally, be sent to the new number. It will also show the new number and the operator on the web site, providing further information to pass on to the police.
So what about the pricing? Track and Protect is a free download and you can use much of the application functionality for free. What costs is the ability to send remote commands, with each command costing a single credit (and remember, because these are sent as text messages, there is a 'real' cost associated them). Credits can be purchased through the Track and Protect website in bundles of 15 (4.99 Euro), 35 (9.99 Euro) and 55 (14.99 Euro). This works out at 0.30 Euro per command, which I think represents excellent value for money. It seems very little to pay when set against the advantages it may give you when your phone is lost or stolen. Theoretically, you can use the application without buying any credits until you need them, but with a starting price of just 5 Euro for 15 credits, it makes sense to enable the full feature set immediately. After all, you don't really want to be wasting time buying credits when you want to get the phone locked as soon as possible.
Conclusion
Track and Protect has been enabled by technology provided by the Dutch company Klomptek. Track and Protect is an example implementation of what can built with their underlying technology. An additional product, Remote Call Manager, which is aimed at SMEs and is equally impressive, uses the same underlying technology to implement a service designed to cut business call expenses. The technology is also available for third parties to create their own solutions and products.
Track and Protect is currently in beta testing. As such, the usual testing caveats apply. However, I did not come across any major problems and the beta label reflects a desire for wider feedback before a full launch rather than the quality of the application itself.
At first glance, Track and Protect's basic functionality isn't really that unique. Most phones have a built in lock code function (though most people don't use it) and there are plenty of location tracking applications around. However, the all round package, the way the features are combined and the robustness of the underlying technology sets a new standard for consumer-focussed security applications. If your phone is lost or stolen, Track and Protect makes it unusable for anyone else and it will provide you with more information, more quickly than any competing solution I can think of. Taken together, these two factors should significantly improve the chance of having your phone returned to you. When you combine the utility and intuitive implementation of Track and Protect with its pricing model, there's very little reason not to install Track and Protect. Recommended.
Rafe Blandford, All About Symbian, 21 Dec 2009
Downlod from Track and Protect website.

Alien SIM card detection
Reviewed by Rafe Blandford at
